While I’m based in Germany, there are several reasons to occasionally surf the web with a Dutch IP address. Since I’m an XS4ALL customer it would seem a convenient solution to use their proxy server. Alas, they do not allow connections from non-Dutch IP addresses. Fortunately XS4ALL also provides shell access to their public UNIX host, so that we can set up an SSH tunnel. (Note that in in this particular case a tunnel may only be used to access XS4ALL services, which is exactly what I want.)
Set up an SSH tunnel
First install and start OpenSSH on your PC if you haven’t already done so. On a Debian/Ubuntu system:
sudo apt-get install openssh-server openssh-client sudo service ssh start sudo insserv ssh |
Now we can tunnel to the proxy, proxy.xs4all.nl, via the shell server, shell.xs4all.nl:
sudo ssh -L 1080:proxy.xs4all.nl:8080 <username>@shell.xs4all.nl -f sleep 3600 |
The -L option tells SSH to forward the proxy port 8080 to port 1080 on our local machine. Then follows the shell server login account (a password prompt will appear). The -f specifies a command to be executed remotely, here a simple sleep to keep the connection alive for an hour.
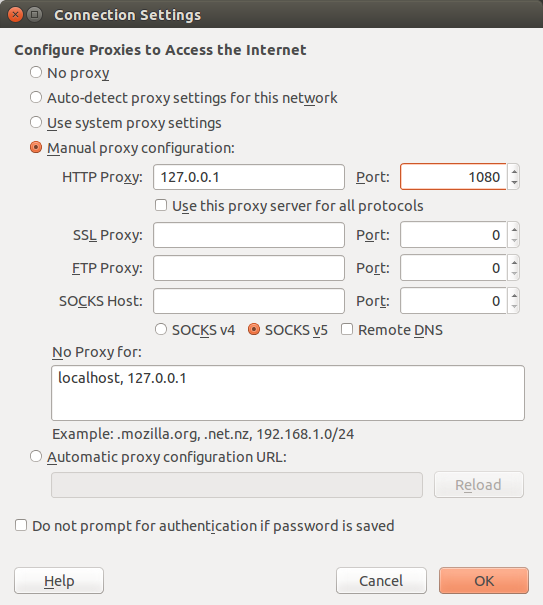
Set the http proxy in your browser: 127.0.0.1:1080 or localhost:1080. Firefox example:
And we’re done!
Chain a local proxy
Now I wanted the same feature for other devices on my LAN, so I decided to set up a local proxy using a Raspberry Pi.
Use raspi-config to install OpenSSH on the Pi.
sudo raspi-config |
Select ‘Advanced Options’->’SSH’.
Install the proxy server, Squid:
sudo apt-get install squid |
To configure Squid for this purpose edit the squid.conf file:
sudo vi /etc/squid/squid.conf |
Grant the LAN clients access to the local Squid proxy. You can probably leave all other ACL entries untouched. For my case I added:
acl myclients src 192.168.2.0/24 http_access allow myclients
Chain the local proxy to the remote proxy that will be accessible via the SSH tunnel on local port 1080:
cache_peer 127.0.0.1 parent 1080 0 no-query prefer_direct off nonhierarchical_direct off
The local proxy will fall back to a direct connection if the remote proxy does not respond properly. If you don’t want this behavior and rather have an error message instead, use this:
cache_peer 127.0.0.1 parent 1080 0 default never_direct allow all
That’s it for the configuration. Set up the SSH tunnel on the Raspberry Pi:
sudo ssh -L 1080:proxy.xs4all.nl:8080 <username>@shell.xs4all.nl -f sleep 3600 |
Restart Squid with our new configuration:
sudo /etc/init.d/squid restart |
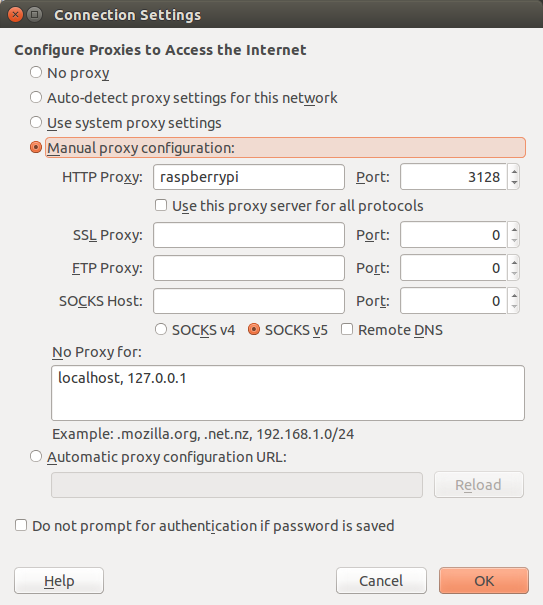
On a PC within the LAN the Raspberry Pi can now be set as an HTTP proxy by its host name or its IP address. Squid listens by default on port 3128 (see squid.conf).
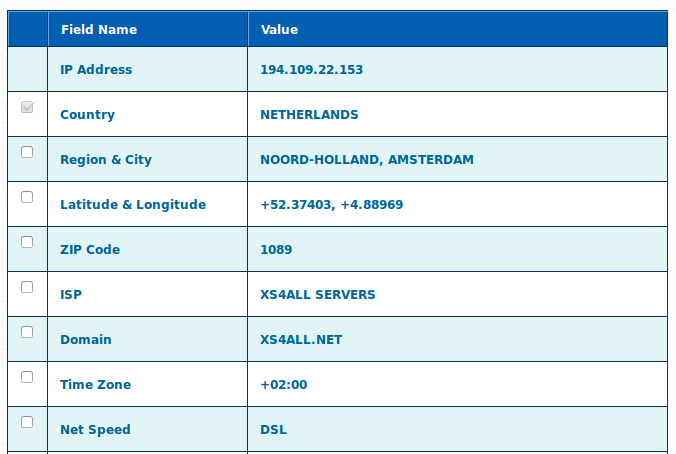
Surf to www.ip2location.com. So there we are. This is me on my German LAN: